39 percent of TU/e falls for fake phishing email
39 percent of people at TU/e clicked a phishing email. Fortunately, it concerned a test by Chief Information Security Officer Martin de Vries and his team, intended to raise more awareness of cybersecurity at the university. In his opinion, the high percentage indicates there’s still a lot of room for improvement in this area.
Since January, phishing emails have been sent to students and staff at all departments and services of the university. 39 percent of them proceeded to do something with that email, such as replying to it, forwarding it, or clicking the link. There are few differences between students and staff, and between the different departments and divisions. De Vries: “This percentage is obviously too high, pretty much across the board. So there’s work to do.”
Phishing is a way in which cybercriminals try to obtain data. “Phishing emails are the way in which a staff member can lose data, share their login with criminals, or get infected with a virus or other malware.” Criminals can then penetrate deeper into the university’s network or use ransomware to shut it down, only releasing it after they’ve been paid a large amount of money. “This behavior puts cybersecurity at the university at risk.”
Text continues below photo.
Training
Students and staff that fell for the phishing email don’t have to be ashamed or afraid of consequences, says De Vries. “Anyone can fall for this. See it as training and learn from it.” The main goal of the test is to provide greater insight into the cybersecurity skills of students and staff. In the time ahead, training courses and campaigns will be devised to reduce the percentage that falls for the phishing emails.
“This result is one of the indicators we’ll ultimately be using to shape our campaigns and training courses. I think it’s a good yardstick, as it provides insight into people’s behavior,” says De Vries. Students and staff can start helping out by completing a survey about their own behavior and the culture of cybersecurity at their own department or division.
“What we are trying to clarify with this survey, is whether users are able to recognize incorrect and suspicious behavior and whether their cybersecurity skills are up to scratch. We’re also taking stock of how people at different departments and services deal with cybersecurity. For one thing, is it discussed at all?”
Clicked
De Vries thinks that most everyone is aware they shouldn’t click a phishing email. “And yet, it happens sometimes, especially when someone’s really busy. So take your time to look at an email and try not to rush things,” says De Vries. Everyone has a button in their Outlook to report suspicious emails, which can also be forwarded to abuse@tue.nl.
People who have clicked a phishing email, which De Vries says happens fairly regularly, must report this to the service desk right away. “Then we’ll check if your laptop got infected and quickly reset the account.”
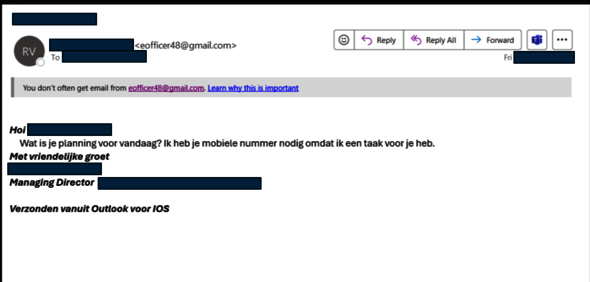
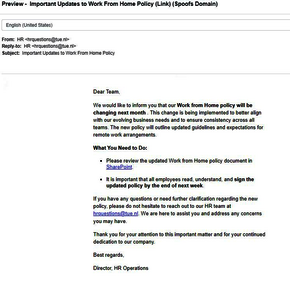
The phishing test
Two examples of phishing emails from the test within the TU/e community. In this case, important telltale signs are the links, of which it’s unclear where they’ll lead, the general salutation instead of a personalized one, and the rushed design. For more information on how to recognize phishing emails, click here (yes, this is safe). Photos | TU/e



Discussion